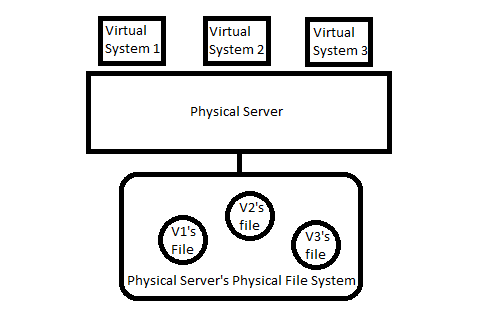
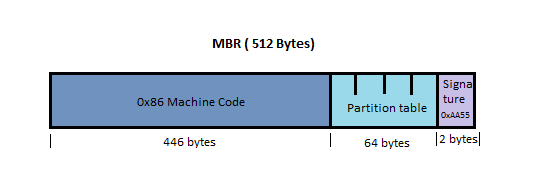
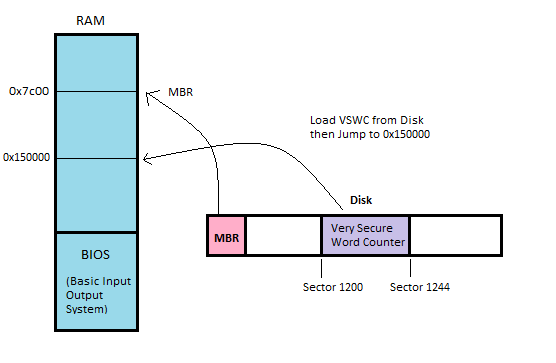
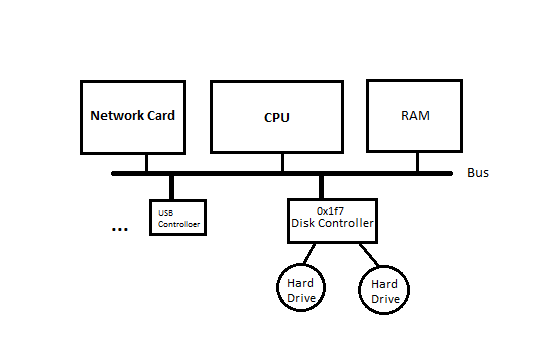
This problem arises because of Moore's Law which states that number of transistors on an integrated chip at min cost doubles every 2 years. Not only chips, disk drives capacity (disk size, not i/o speed) is also getting larger at a fast speed. However, because of the effect of incommensurate scaling, it becomes hard to balance all the resources and to get the most out of it and there's a gap between hardware capacity and design capability.
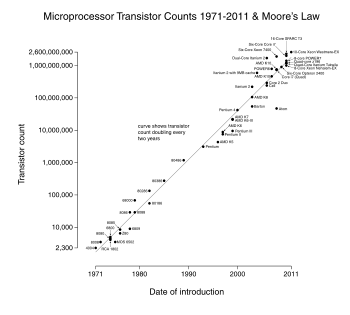
Moore's Law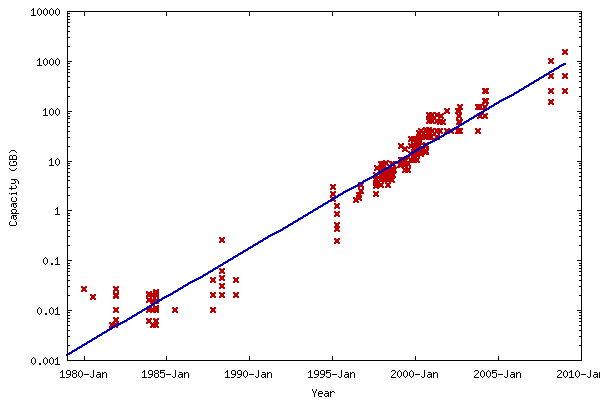
Hard drive capacity
The good news is that technology grows exponentially or d(technology)/dt = k×technology . This is because people can use advanced technology to develope more advanced technology. A better computer that can do faster computation can solve more complicated or bigger problems. For example, the very first successful computer UNIVAC had an Error Correcting Circuitry (ECC) for almost every chip in it. They had to have all the ECCs because they didn't have simulators and they were not sure what kinds of errors would occur. To make it simple, they just added ECCs. When simulater was later developed, they were able to throw away many ECCs by simulating.