When one side of a waterbed is pushed down, the other side is pushed outwards. This is an analogy to the tradeoffs often seen in technology. If one area is improved on, often another area gets worse. One example is the time-space trade off in sorting. A searching algorithm can maximize efficiency in time or space, but not both.
Sorting a 10GiB array of 1KiB items would require additional data swapping using quicksort. This would increase the time but reduce the memory requirement. By optimizing using another sort such as sorting pointers instead, it would decrease search time but increase memory usage. This will save time by not moving around 1KiB objects around in memory.
This is also seen in security. There is a tradeoff in the matter of hardware tokens vs. passwords, as passwords can be guessed but are free, and hardware tokens are not guessable, though they cost money to buy and replace.
This occurs when a change in one part of a system causes an unanticipated change in another part. It occurs both in designed systems and chaotic systems. Consider in multi-byte encoding for Japanese characters. A file name using a kanji character that uses multi-byte encoding may part of its encoding to be the same as the encoding as the ‘/’ delimiter. This would cause issues when parsers look at the kanji character and instead of reading the entire multi-byte character, it reads a character split with ‘/’.
If the symbol 字 happens to have a part of its byte encoding to be the same as “/”, a simple command such as $mv foo xy字bar would cause an error.
UTF-8 fixes this issue of character encodings overlapping. It is also possible to change the kernel so that it recognizes multibyte characters.
Another example is backing up a partition in a container-based virtual system. A self contained host can't read from other hosts, but while root is running $tar cf backupdevice /hosts, the function stat("f", filename) is run before open("f", filename), and if stat shows that the file is a regular file, then the file is copied. This would normally not allow links to files on other hosts, but the malicious user could replace his regular file with a link to another host's password file between the time stat and open are run. A solution is to open the file first and then run stat, but this also has a security problem. It is up to you to figure out what that is.
A system can develop new and unanticipated properties as it scales larger or in more complex systems. One example is the Tacoma Narrows Bridge. The wind hit the bridge at the resonant frequency and the bridge began bending. This bending is usually acceptable for smaller bridges, but in this case, the large bridge collapsed.
Computer worms are an emergent property. When the internet was much smaller, it was not worth it to develop a worm to spread to only a handful of computers. Nowadays, worms can spread throughout the vast internet.
Another emergent property: piracy on dorm internet connections.
Scaling is a big deal, and if not every component scales at the same rate, unexpected problems can arise. Animals cannot grow infinitely large. The strength of their bones can only handle a specific proportion of weight. This is because the strength of bones is proportional to the square of an animal's height, which is because the strength of bones is related to bone surface area, while weight is proportional to the cube of height.
Economies of Scale: - cost advantages due to expansion. Example is the pin factory from Adam Smith's book, The Wealth of Nations. Another example is reading files one byte at a time vs. reading them in larger chunks faster.
Diseconomies of scale:- cost disadvantages due to expansion. An example is a star network. As the number of users connected to a hub or a switch increases past 100, the hub that can handle the traffic is much more expensive because of the incommensurate scaling. A regular hub or switch can't handle the traffic.
Why?
-
Moore’s Law states that the number of transistors on a chip doubles roughly every two years.

-
A corollary, Kryder’s Law, states that the storage density of hard drive disks doubles annually
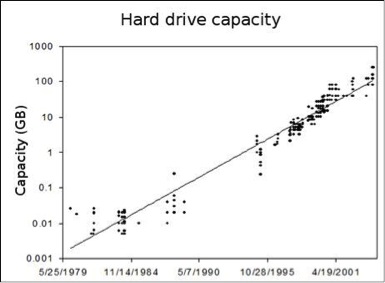
Analysis: Both laws can be seen to be roughly growing linearly at a logarithmic rate.