Lecture 18 - Confidentiality, Authorization, and Protocols
By Howard Lee
Authentication and Encryption
Kerckhoffs's design principle for cryptosystems
Kerckhoffs's principle was stated by Auguste Kerckhoffs in the 19th century, which states that a cryptosystem should be secure even
if everything about the system, except the key, is public knowledge.
The basic idea of the principle is to minimize what needs to be kept secret.
e.g. ssh from user view point
CLIENT
- ~/.ssh/id_rsa.pub public key
- ~/.ssh.id_rsa private key(RSA)
- ~/.ssh.known_hosts
The private key(RSA) which is encrypted via passphrasemust must be secret,
and the know_hosts has some privaxy issues but not autheticated.
SERVER
Note: $cat .ssh/* is a dangerous thing to do since it will display user's ssh private key on the screen which ppl can take a photo
of it and obtain user's private keys.
SSH Transport Layer:
Initial key exchange typically RSA
- public key
- includes server authentication
- establishes a private key reoccurs every hour
User Authentication Layer:
public key or password?
disadvantage for password: password guessing/video source typing
advantage for public key: two factors authentications needed, id_rsa(private key) and passphrase
Problem with SSH as a Protocal/Software System:
- tempting to just use passwords (less secure)
- heavy weight operations to get a connection
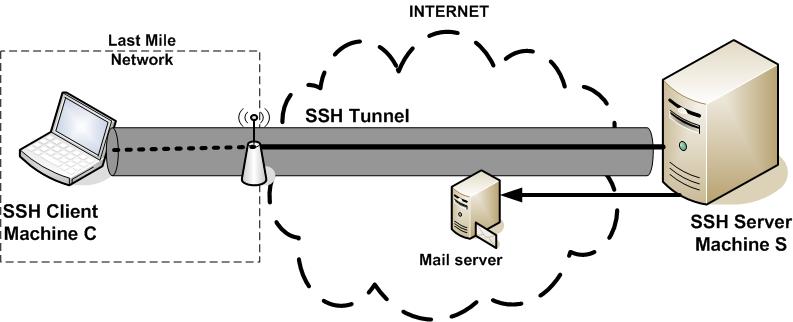
SSH Tunnel (port forwarding)
Computer networks use a tunneling protocol when one network protocol (the delivery protocol) encapsulates a different payload protocol.
By using tunneling one can (for example) carry a payload over an incompatible delivery-network, or provide a secure path through
an untrusted network. In another words, ssh tenneling creates a virtual connection between client and server.
Problem: has troubles scaling to large corporate environments.
Internet Protocol Security (IPsec)
a protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication
session. IPsec also includes protocols for establishing mutual authentication between agents at the beginning of the session and
negotiation of cryptographic keys to be used during the session.
- much bigger +grander
- key distribution + management
Tunneling is common in key,Virtual Private Network(VPN) out of tunnels. Don't have to worry security much since it's a private network.
Authentication
Access control (Authorization)
Direct control
- Hardware checks each access to resources, so it can be done
quickly but can only be done with simple rules.
- Access is mapped into the address space (e.g. virtual memory).
The principal is only allowed to access within its address space.
Indirect control
- It is done by issuing service requests (e.g. syscalls.).
- It is handled via trusted codes (e.g. kernel).
- OS checks each access to resources, so it's very flexible but it
is slower than direct control.
Goals:
- privacy(data) no output data access
- integrity(data) no input data access
- trust (between program and data) can we delegate the authorization?
Basic Questions:
1. what is your security model? (objects, principals, eights)
2. what are the threats? (mostly insiders/what may go wrong inside?)
3-D (x,y,z)= (users, files, ops) , Large data, need huge array /must be correct and secure
- storage overhead
- common patterns
e.g. simple pattern: Unix model
- owner 1 person
- group 1 group
- other everybody else
Assume we make rwx for each of them, which file: read write execute and dir: read write search.
We put files for cs111, cs130,etc on web server at UCLA
www/cs111 <----------- owner (eggert), group(cs111_ta), other(student)
make rwxrwxr-x
We have /etc/groups ---> store whose in what group
PROBLEM: who can modify /etc/group? ANS: root, but this doesn't scale.
Access Control List(ACL)
An access control list (ACL), with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies
which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry
in a typical ACL specifies a subject and an operation. getfacl and setfacl can be used to get and set the file's ACL, respectively.
ACLs are manipulated by syscalls, and they can only be manipulated by the file's owner. The professor could have used ACL and manipulated
the files in the directory so that only he and his TAs can access them. This would not require a help from the server administrator, since
the professor is the owner of the files.
Advantages:
more flexible, easy to admin, some overhead.
Disadvantages:
users get too many rights, big rights bundle per user/ uses become targets.
Problem:
If you are porfessor, you can do too much programs that run as eggert should be more limited.
Role-Based Access Control (RBAC)
Role-based access control (RBAC) is an approach to restricting system access to authorized users and sometimes referred to as role-based
security. Within an organization, roles are created for various job functions. The permissions to perform certain operations are assigned
to specific roles. Members of staff (or other system users) are assigned particular roles, and through those role assignments acquire
the computer permissions to perform particular computer-system functions. Since users are not assigned permissions directly, but only
acquire them through their role (or roles), management of individual user rights becomes a matter of simply assigning appropriate roles
to the user's account.
e.g. professor, sysadmin, student <-------rights are associated with roles, not directly with users.
Access Control Lists (ACLs) vs. Capabilities
Capabilities and access control lists (ACLs) actually have a fairly symmetric relationship: in an access control list model of security,
the authorities are bound to the objects being secured; in the capabilities model, the authorities are bound to objects seeking access.
So if the objects are laid out in a table, with the access-seeking objects across the top and the security-seeking objects down the side,
the columns represent sets of capabilities, and the rows represent individual access control lists.
-
ACLs guardians of data that reside next to data (Unix access rights for files(3-entry ACLs))
-
Capabilities guardians of data that reside to process
ACL's
- Associated with an object and checked on each access at any moment in time
- Size is unbounded
- Centralized repository of who has rights to this object.
Capability-
Convenient handle for an object
- OS lets you filter out rights easily
- You can't forge them easily
Unix file descriptors are similar to capabilities. Like capabilities, file descriptors only have one set of rights for the file.
File descriptors can be easily given to another program by using fork. Finally, file descriptors have faster access checking than
normal files. Unix systems uses both ACLs and Capabilities.
2 handle that gives you the right to access an object <------ access rights in file descriptors
example:
fd = open("/etc/passwd", O_RDONLY); <----------- ACL check, might be on disk which might be
read(fd,buf,sizeof buf); <---------- capability check (OS looks at a bit in file descriptor), this is fast. The bit cannot be changed which you can cache
fd = open("/tmp/f", O_RDWR|O_CREAT, 0000);
write(fd, buf, sizeof buf);
Capability:
+ faster(rights can be cached)
- revoking is harder
ACLs vs. Capabilities over a Network Server that has ACL
Capabilities over a network server are typically an encrypted hash.
long unguessable integer
- ----> server new object
- -----> client must keep int secret
- ------> check reg has int?
Capabilities let client delegate access.
e.g. eggert can give Kobe a write capability to grades file.