Hongchen Yu
Direct
Access
Application is given a direct pointer to hardware,
access check is only done when the pointer is created. This approach
is often done through virtual memory
Advantages:
- Fast access
(since we are working directly with hardware)
Disadvantages:
-
Resource can be more easily corrupted (our application will rely on
hardware checking, which is often not enough)
Indirect
Access
Application gets a handle instead of a direct pointer
to hardware
Advantages:
- Have access control (can revoke
access control)
Disadvantages:
- Slower access (not working
directly with hardware
Examples of indirect access:
File
descriptors
Goals of
access control
Privacy
Integrity
Trust
Sharing
Note:
defending against DoS attacks is not a goal of access control
Access control
characteristics
Access control structures keep track of what
access are allowed, there are several models of access control,
however, they all share the following in common:
- Access control
data itself must be updatable
- Updating such data must be a
controlled operation, since the data is sensitive
- Access control
data must be unforgable (thus, at least part of it must be in OS)
-
They access control must control all access. In other words, they
must be consulted before every access (or else it can just be
bypassed)
- From the above, we can infer that it needs support
from hardware and/or OS
The access control problem can be visualized in the following way. There are many principles, operations, and objects. The access control structure must specify what operations can each principle do on each object. Since we have three dimensions (principles, objects, operations), we can represent the above problem with the following 3D space.
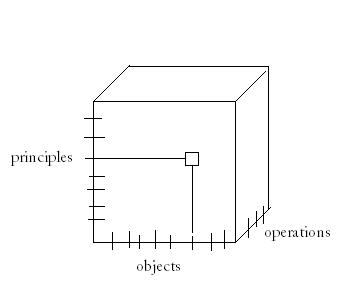
This space can be represented by a 3D array of booleans, where at each specified point, the boolean is true if the principle can do the operation on the object, and false otherwise. We can represent any state with the above representation, however, it uses a lot of memory. With that in mind, there are two models of access control that are commonly used, Access Control List (ACL) and Capabilities
Access Control
Lists (ACL)
There are several models of ACL, we will look at
the Unix Permission model, the Windows NT model, and Role Based
Access Control (RBAC)
UNIX
permission model
This model is very simple and compact, it is
constructed as follows:
- There are 3 operations (read, write and
execute)
- There are only 3 principles (user, group, and owner)
-
Each object has 9 permission bits (3 for each principle)
The way
the principles work differs slightly in the traditional approach and
the modern approach
- Traditional approach: each process can only
be in one group. This can be some what limited if a process needs to
have the permissions of multiple groups.
- Modern approach: each
process can be in multiple groups. Now a process can have permissions
from multiple groups, but there is no restriction on access between
groups. This may be a bit too generous in many cases.
Windows NT
ACL
Although this model is originally implemented on Windows,
it is now adopted by many Unix-like OS, such as Linux and Solaris.
In
this approach, associated with each file is a list of users that can
access it. On your Linux machine, you can view these permissions
through the getfacl command. We can also change permission with the
setfacl command.
Role Based
Access Control (RBAC)
This access control determine a user's
access rights based on what role the user assumes. RBAC has the
following properties:
- All rights are associated with roles
-
A user can assume multiple roles
- A user may gain/loss rights as
the user switch between different roles
Capabilities
Capabilities
revolves around the idea of possession of "words" that
grants a user certain rights. These words are often constructed with
checksums, which are practically unforgable. Capability system has
the following properties:
- Usually implement using encryption (to
generate the words)
- Rights can be passed around by passing the
word associated with such rights
DoS the a kind of attack (over a network) that excessively floods a certain service to render it unavailable.
Defense against
DoS
- Captcha: we can separate bots from human users in order to
filter out some attack queries. However, this many not be that
effective since the attacker can just flood the captcha service
instead.
- Blacklist IP - we can deny service to IP that are
suspected to be attackers.
- Change IP Dynamically - sometimes the
DoS attack is hardcoded to improve performance of the bots (skipping
DNS to save resources), thus if our server changes IP once in a
while, it might be able to avoid incoming attacks.
- Make web
server faster - add more resources to our server to make it harder to
crash.
With the major advances in multicore technology, many web services have resorted to multithreading to improve speed. Here is a list of some methods of multithread
Fork – slow
Thread - fast, but share memory may allow some buggy script to corrupt all the shared memory
Pre-forked children - make many children in the beginning to wait and do work, if one child terminates, it will not interfere with the integrity of the system
Event-based with non-blocking IO - running multithreaded, each thread associated with a CPU. Scheduling is handled by the application, and the designers design the scheduler in a way so that the threads never wait.