Scribe Notes: Lecture 17
Vasilios Mezinis and Ryota Shibano
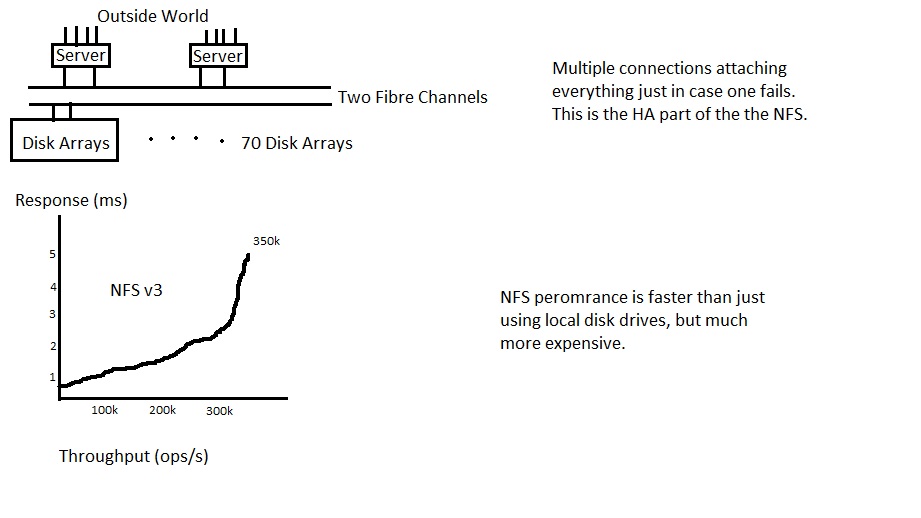
NFS performs:
· SPECsfs20082008_nfs.v3
· HPBL860c i2 4-node HA-NFS cluster (2010)
· 4 servers (each has 2 boot drive and 192 GB Ram)
· 8 disk controller (each has 2 GB cache)
· 4 FC switches, 16 disk array, 1472 drivers, each has 72 GB

NFS Security:
Client A wants mount or un-mount without constantly having to go back to root by plugging in a NFS machine and allowing everyone to use it.
Steps for Client A to become root:
· $ sudo sh
· # cp /bin/mount /nfs/eggert/mount
· # chwon root /nfs/eggert/mount
· # chmod uts /nfs/eggert/mount
· # ls -l
Steps for Client B:
· $ /nfs/eggert/mount ______ ______
For this method to work, we must assume root access people on all clients are completely trustworthy. In reality, this method won’t work because it can only happen highly managed, small groups. We cannot assume everybody is trustworthy.
Method to Solve the Problem:
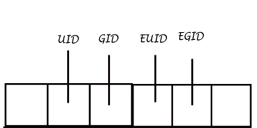
Make root have a UID of 0 and “nobodies” have a UID of 65535 (or any non-zero number). Clients with UID of 0 have access to all files and can change anything at will. Clients with UID that are no equal to 0 have access to only files that are public. This avoids the problem because clients without UID of 0 cannot use chown or chmod.
You can impersonate any used when root. There needs to be authentications that goes beyond just trusting a person's UID number. (NFS solves this problem, and we will learn how later.)
Suppose Client A says that Eggert's UID = 59 and Client B says Eggert's UID = 193. Causes problem of files not being able to be shared across the two different sectors since they are associated with different UID's. We can solve this by using name instead of UID's! However, its tricky to program since strings can be of infinite length. This method is used in NFS v4, but is slower.
The most common problem in NFS, however, occurs when the error "Network not responding, still trying." appears on the screen. This occurs when too many people are using the same network, or when the network itself is down. It occurs when the server is trying to contact the outside world.
Security:
Security cannot be easily retrofitted and should be though about before programming even begins
The real-world meaning of security: Defense against attacks via force and fraud.
The virtual-world meaning of security: Fraud is currently the big problem. However, force must not be overlooked.
Main forms of attacks:
The attacks are against privacy (passwords), integrity (changing a students grade), and service (making a system perform badly).
To solve this problem: We want to disallow unauthorized. However, we still want to allow authorized access! These are usually conflicting goals, which, individually, could solved easily. However, together, they prove very difficult to maintain.
It's easier to test authorized access because if a person like the chancellor of UCLA cannot access the documents, he will tell people and the problem will be solved. Hard to test unauthorized service because if a hacker gets into the server, he will not be telling anyone.
Threat Modeling and Classification:
Don't just design system with passwords. It is necessary to figure out the possible threats to a system, and the design your programs around those exact threats.
Example: For Citibank, the biggest problem is problem is people in the inside miss using their authority!
Types of Attacks:
Insider Attacks: People have access to the passwords of the system use them inappropriately. A lot of times if they are caught, the company does not tell the public because they are embarrassed.
Social Engineering: Where someone pretend to be someone else. For example, when a student pretend to be a teacher to change his grades.
Network Attacks: Buffer overloads, viruses (e-mail and drive by downloads), denial of services. These are getting worst, not better.
Device Attacks: Attacks initiated through a USB of CD.
Functions for Implementing Security Measures:
Authentication: Check to see if the user is who they say they are. Do this through passwords for example.
Authorization: What is any given user allowed to do. This is implemented through permissions on files.
Integrity: Detect when someone attempts to change information in a file. Keep an eye on this through checksums and logs.
Auditing: Detect suspicious patterns of activity that, though they may have not done anything wrong yet, has the potential to be harmful. This is checked through logs that look suspicious. For example if someone is constantly accessing a famous person information page in a hospital.
Correctness and Efficiency: People won't use the system if it wrong or if it takes to long to use. Need the balance the above four while maintaining this.